IROS 2021
Hidden Motion Signatures in Multivehicle Swarms
Abstract: A resilient multi-vehicle system cooperatively performs tasks by exchanging information, detecting, and removing cyber attacks that have the intent of hijacking or diminishing performance of the entire system. In this paper, we propose a framework to: i) detect and isolate misbehaving vehicles in the network, and ii) securely encrypt information among the network to alert and attract nearby vehicles toward points of interest in the environment without explicitly broadcasting safety-critical information. To accomplish these goals, we leverage a decentralized virtual spring-damper mesh physics model for formation control on each vehicle. To discover inconsistent behavior of any vehicle in the network, we consider an approach that monitors for changes in sign behavior of an inter-vehicle residual that does not match with an expectation. Similarly, to disguise important information and trigger vehicles to switch to different behaviors, we leverage side-channel information on the state of the vehicles and characterize a hidden spring-damper signature model detectable by neighbor vehicles. Our framework is demonstrated in simulation and experiments on formations of unmanned ground vehicles (UGVs) in the presence of malicious man-in-the-middle communication attacks.
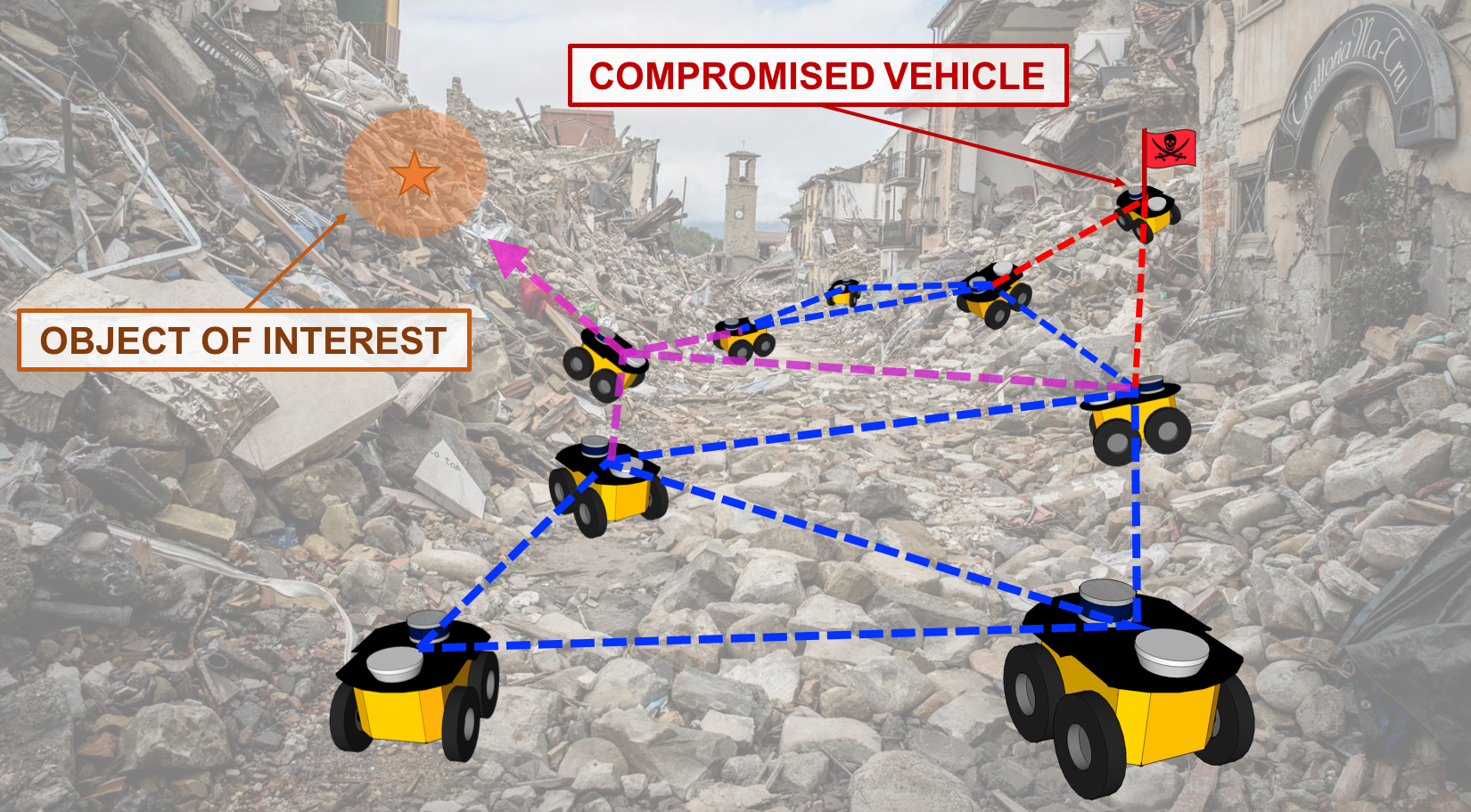
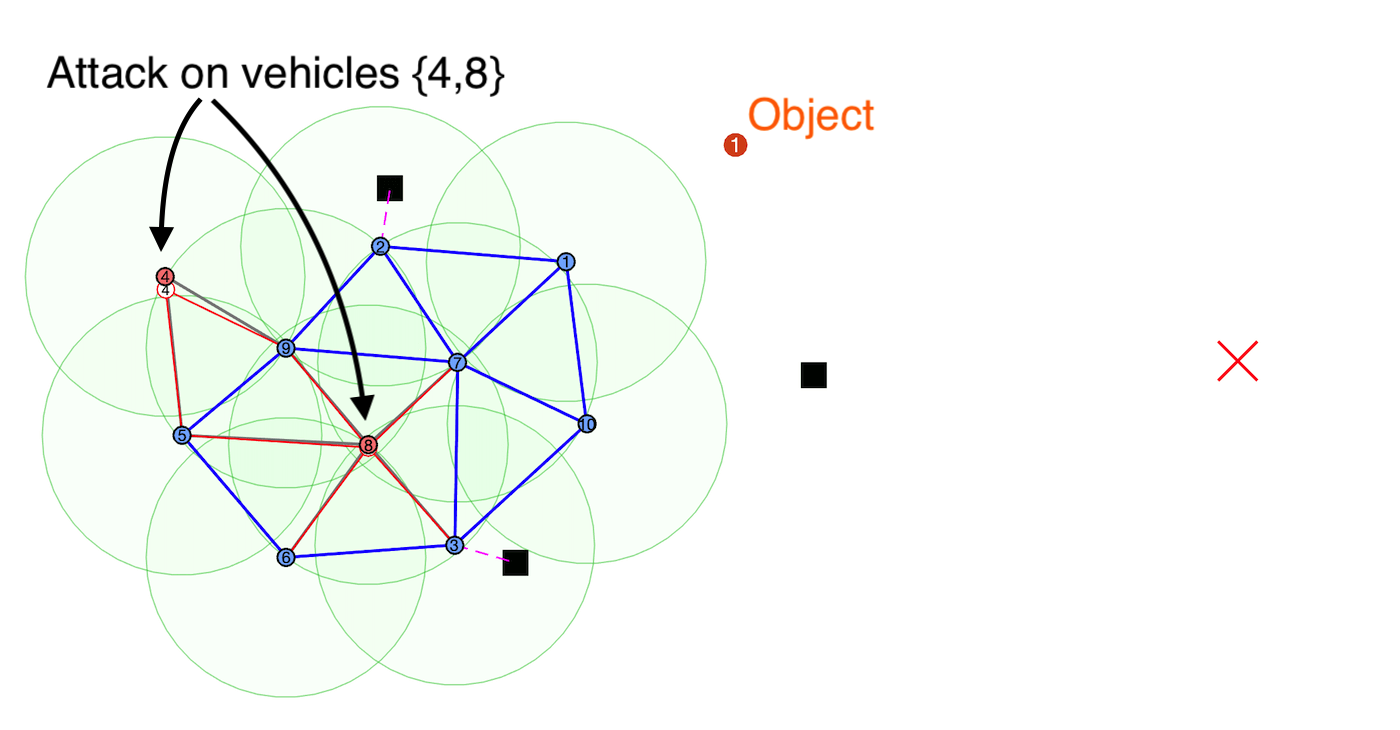
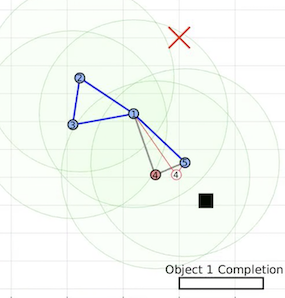
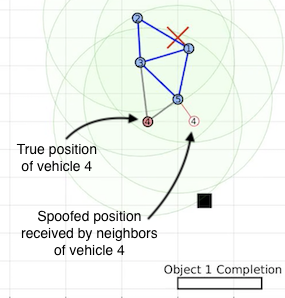
Generally, applications that leverage multi-vehicle networks assume that all vehicles are cooperative while performing desired operations to maintain swarming formations and can exchange all necessary information to complete a task. However, these vehicles are susceptible to malicious external cyber-attacks that can affect system performance or intercept safety-critical information. We propose to utilize a side-channel information exchange that contains hidden data for vehicles in the network to detect that is unknown to potential attackers.
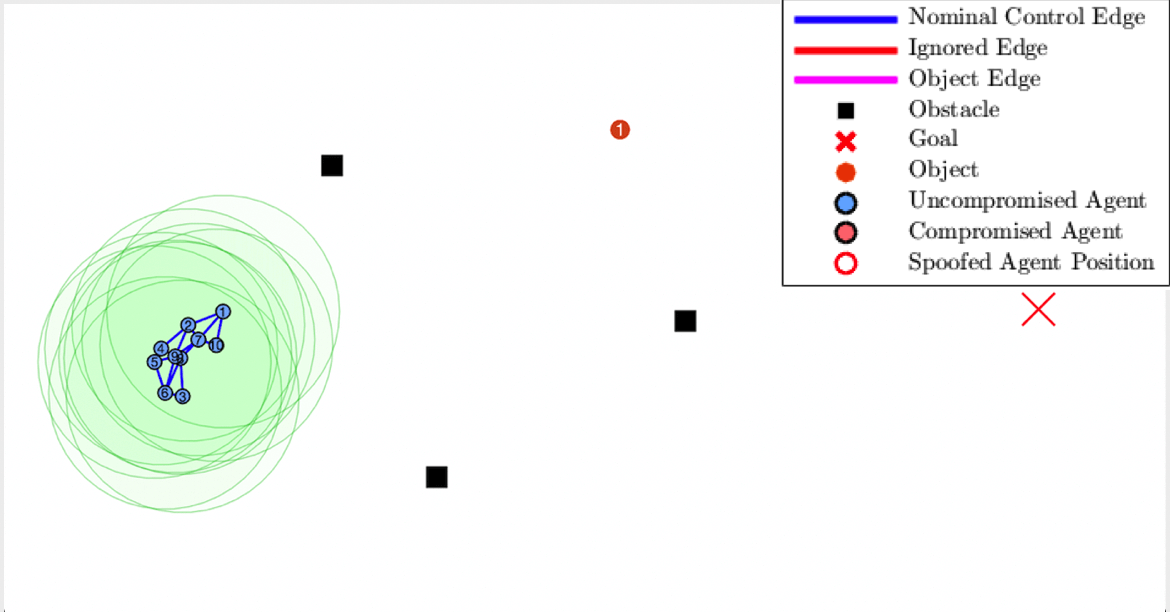
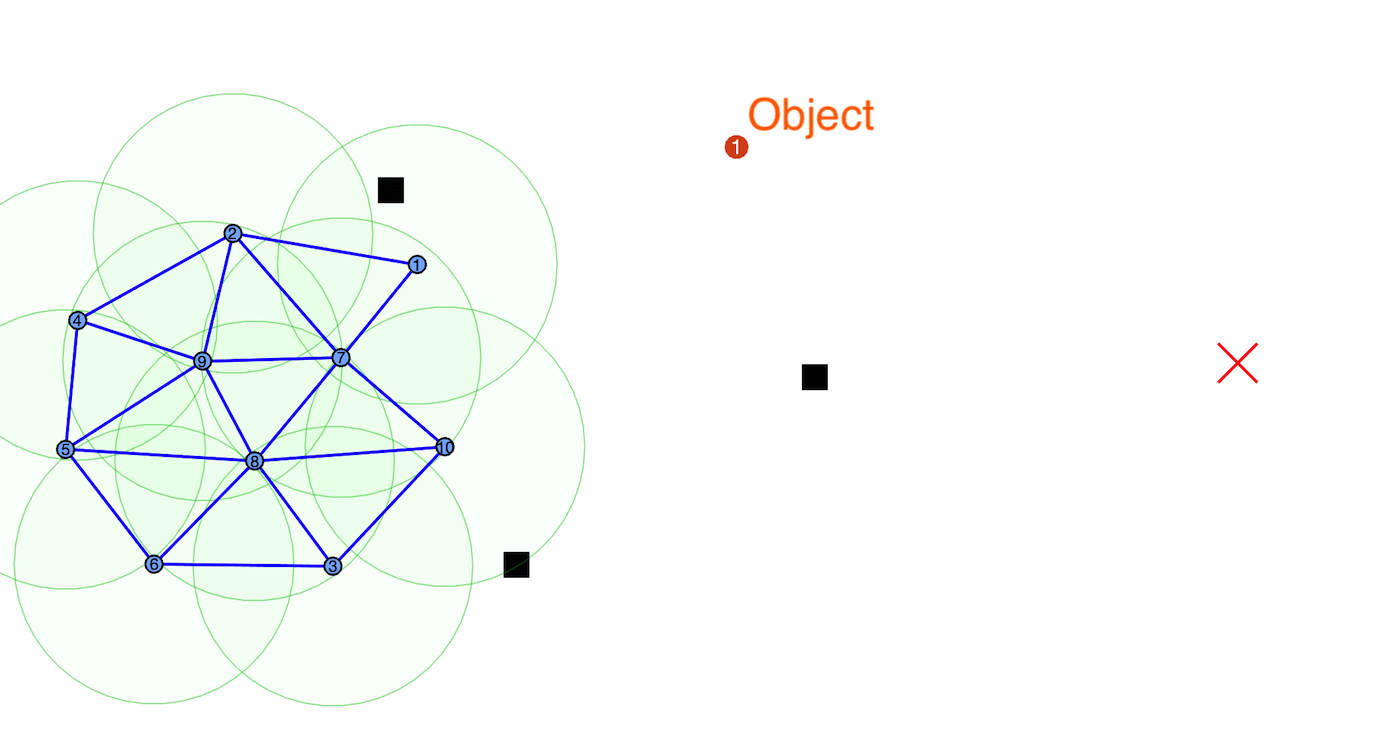
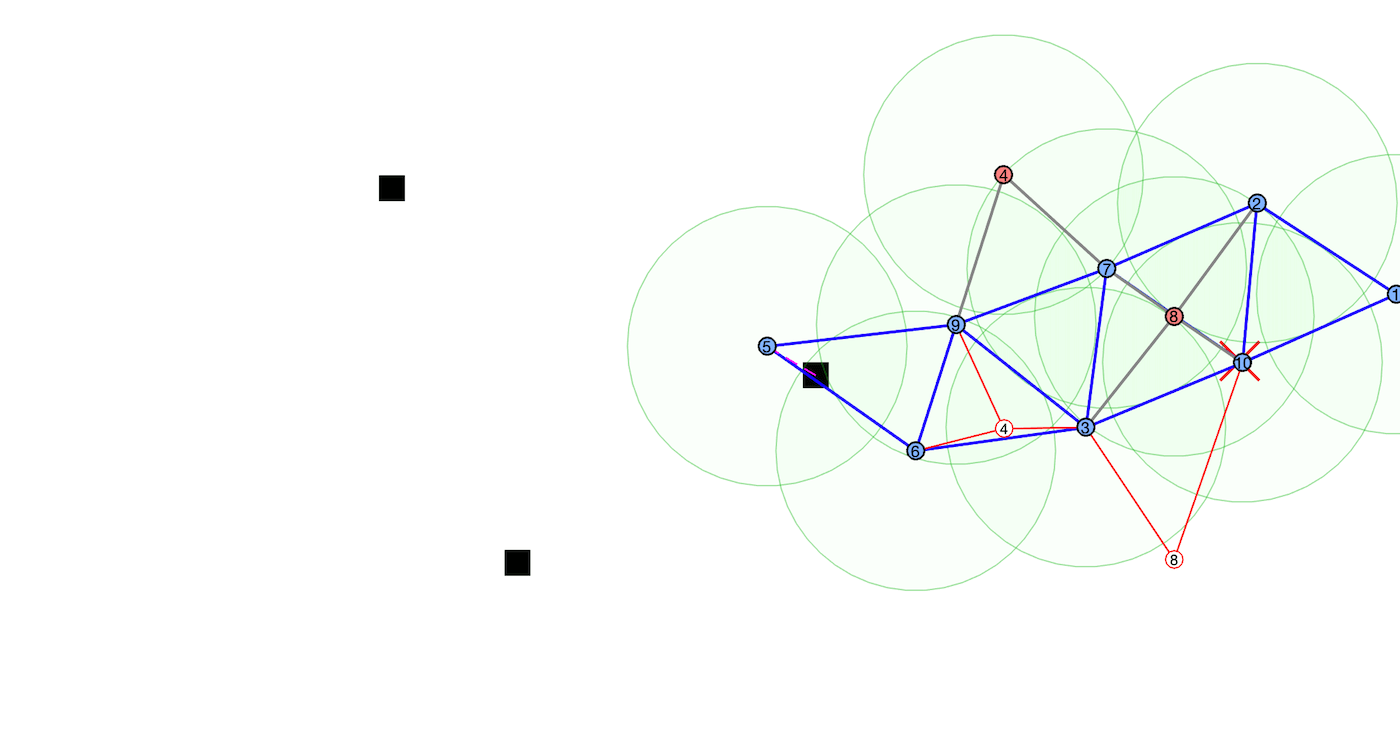
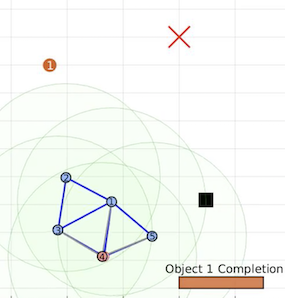
Virtual spring-damper meshes for proximity-based formation control are leveraged for both
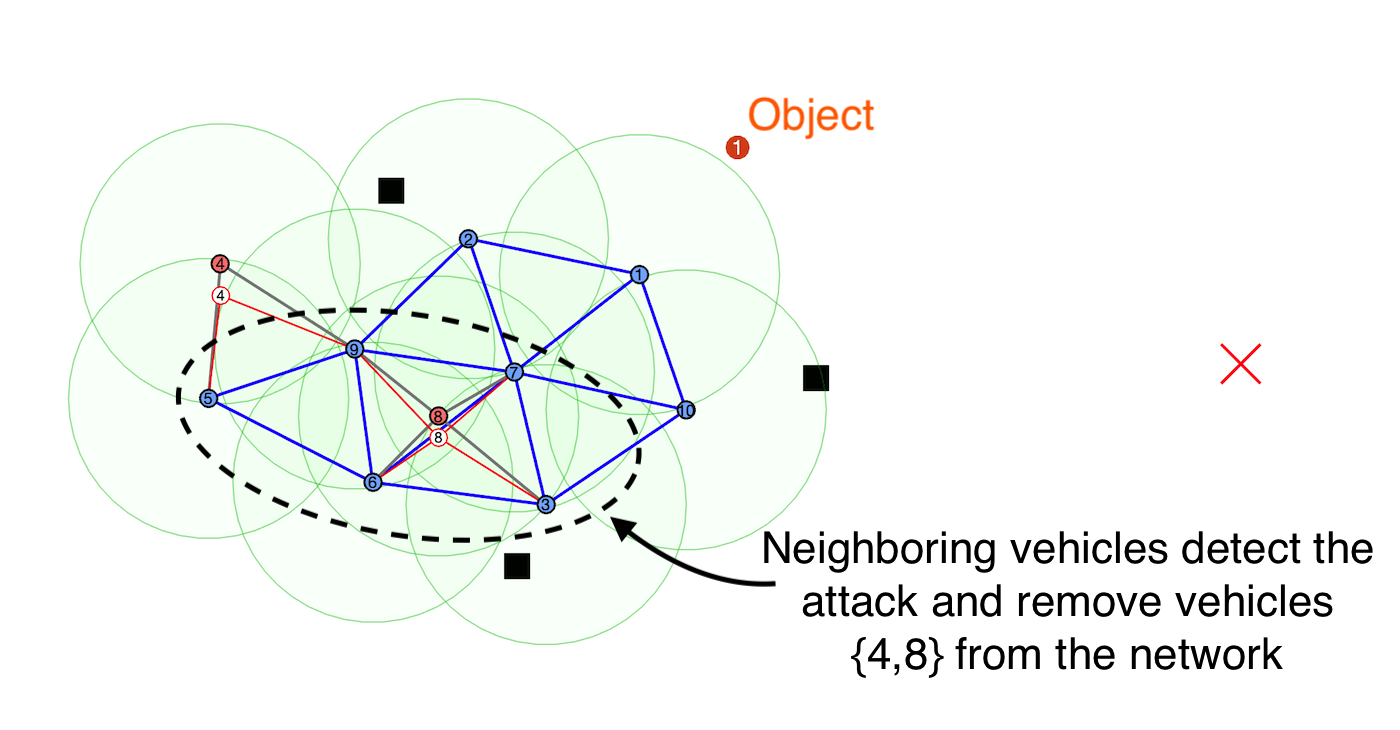
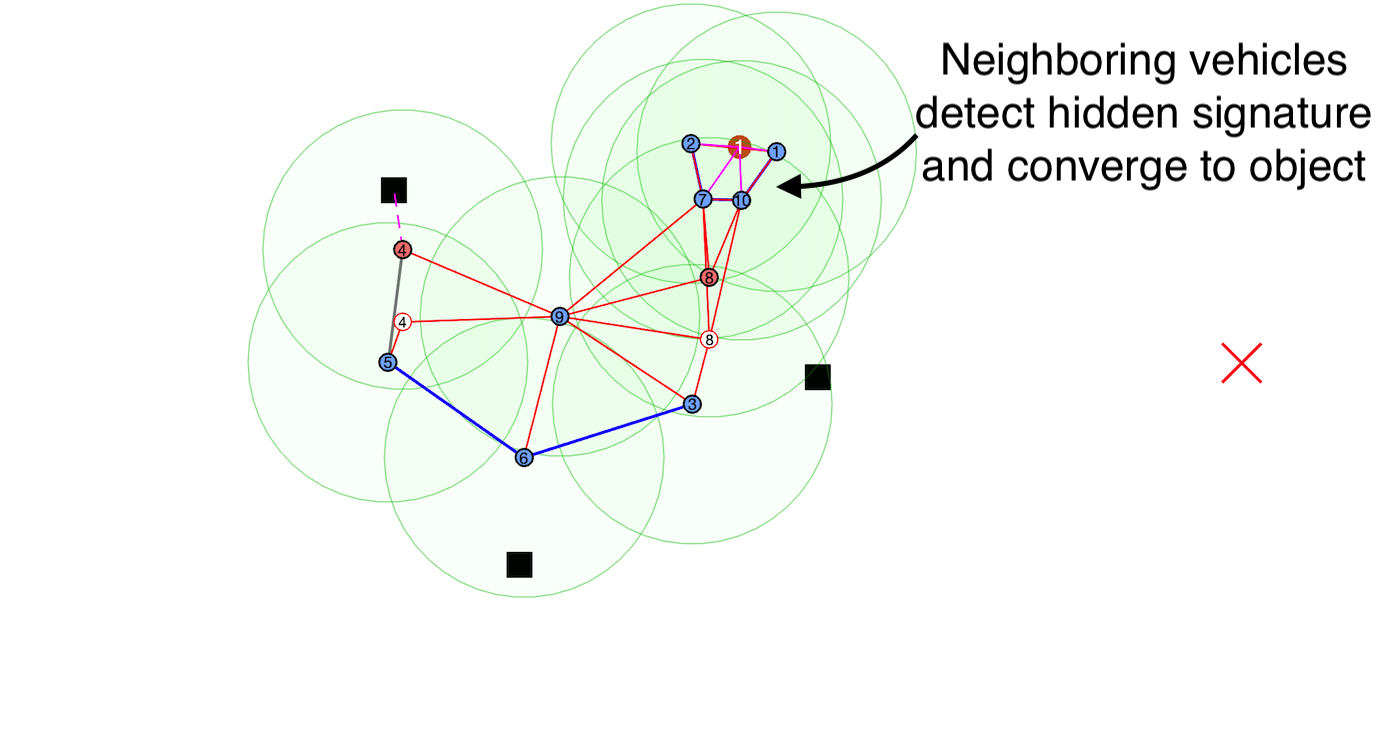
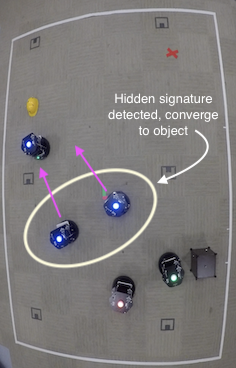
detection of misbehaving vehicles and also any hidden signatures that are being passed
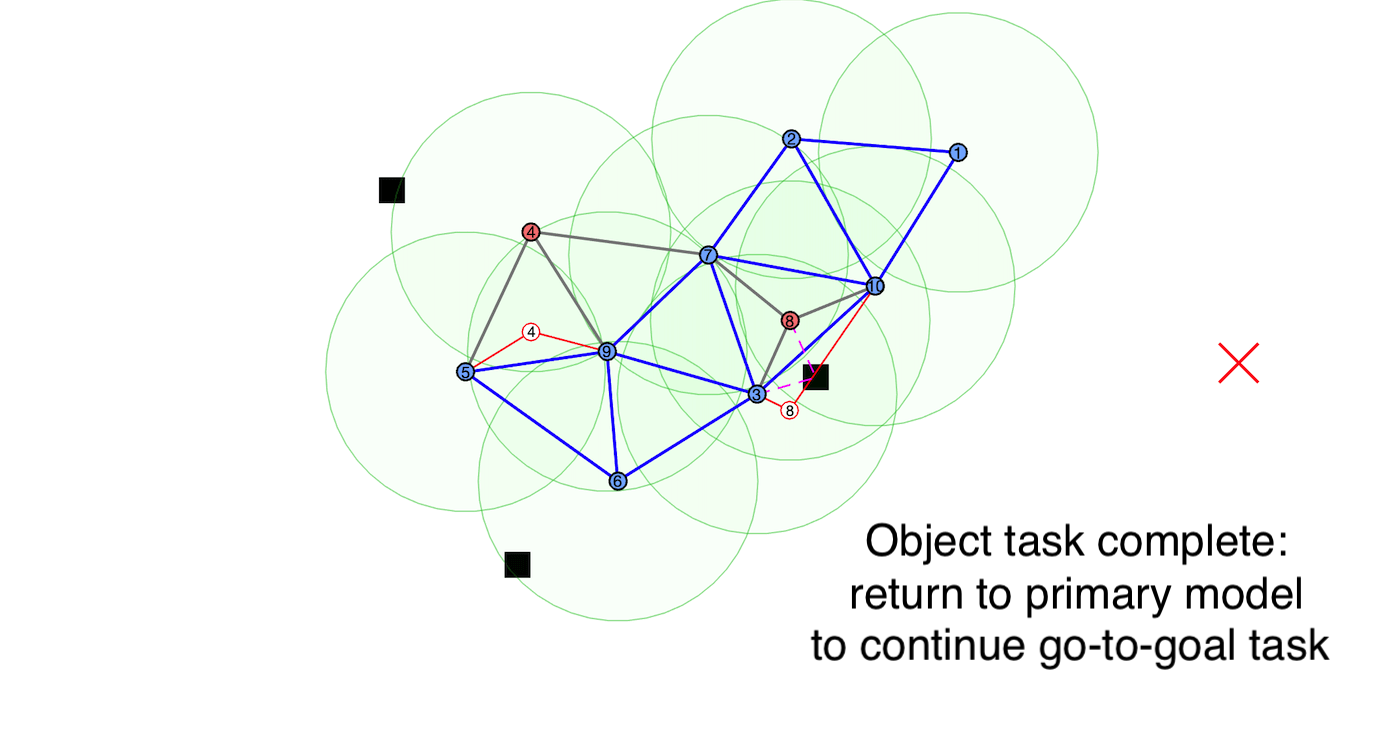
from nearby vehicles. In our work, we apply our framework to applications where mobile
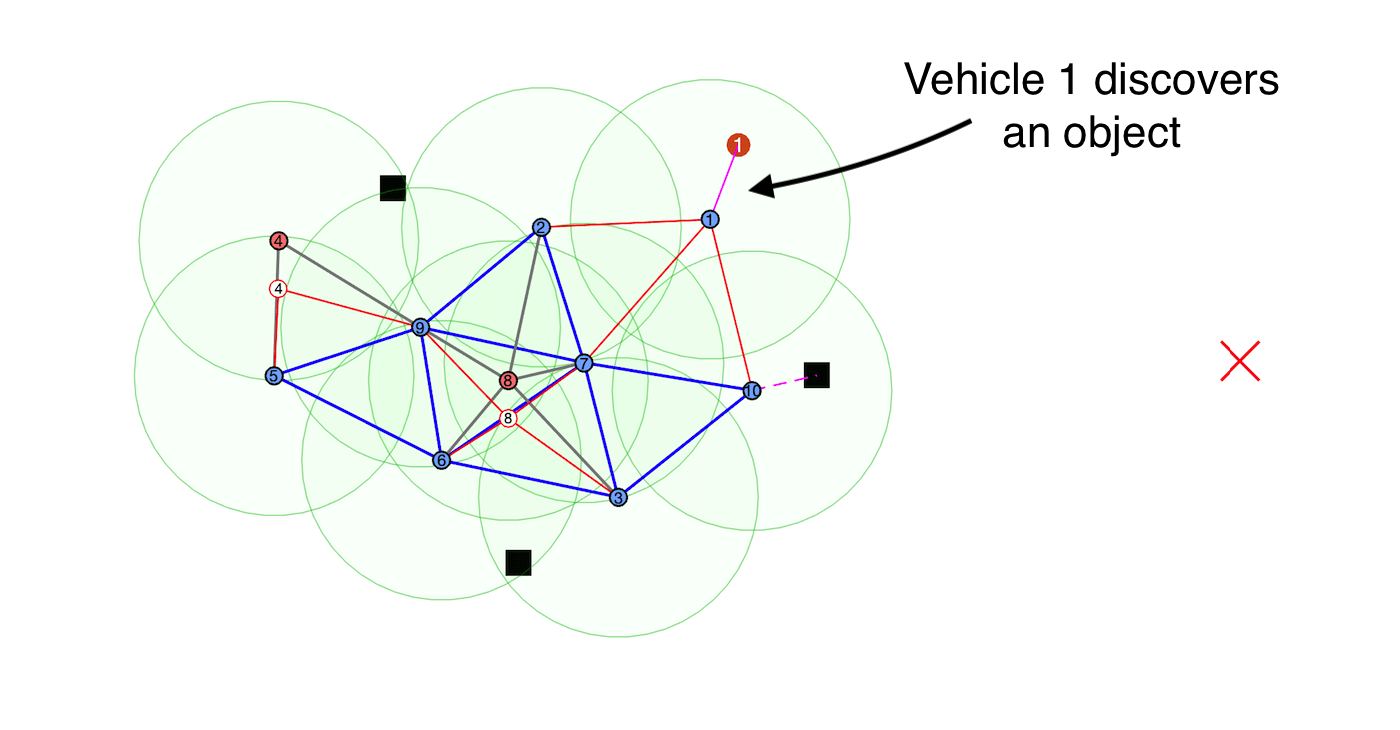
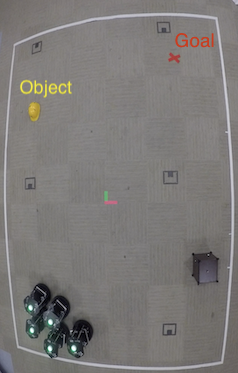
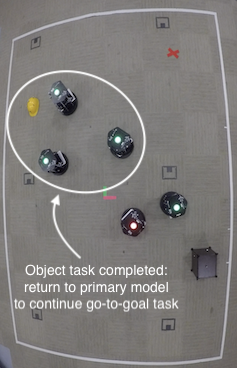
robotic teams relay safety-critical information concerning any discovered object of interest
to the remaining vehicles by utilizing hidden signatures to maintain secrecy from potential attackers.
More details about our framework can be found in our accepted paper [IROS '21].
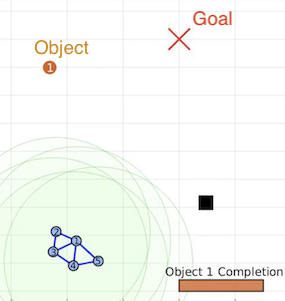
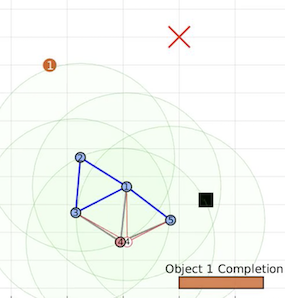
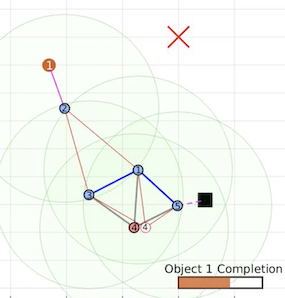
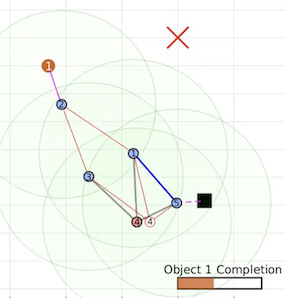
Further simulation and experiment videos can be viewed from the following webpage. Below
are a sequence of snapshots from both a Matlab simulation and a lab experiment using TurtleBot2 robots.