IFAC 2020
Cumulative Sign Sensor Attack Detector
Abstract: Stealthy false data injection attacks on cyber-physical systems introduce erroneous measurements onto sensors with the intent to degrade system performance. An intelligent attacker can design stealthy attacks with knowledge of the system model and noise characteristics to evade detection from state-of-the-art fault detectors by remaining within detection thresholds. However, during these hidden attacks, an attacker with the intention of hijacking a system will leave traces of non-random behavior that contradict with the expectation of the system model. Given these premises, in this paper we propose a run-time monitor called Cumulative Sign (CUSIGN) detector, for identifying stealthy falsified measurements by identifying if measurements are no longer behaving in a random manner. Specifically, our proposed CUSIGN monitor considers the changes in sign of the measurement residuals and their expected occurrence in order to detect if a sensor could be compromised. Moreover, our detector is designed to be a memoryless procedure, eliminating the need to store large sequences of data for attack detection. We characterize the detection capabilities of the proposed CUSIGN technique following the well-known chi-square failure detection scheme. Additionally, we show the advantage of augmenting CUSIGN to the model-based Cumulative Sum (CUSUM) detector, which provides magnitude bounds on attacks, for enhanced detection of sensor spoofing attacks. Our approach is validated with simulations on an unmanned ground vehicle (UGV) during a navigation case study.
Today’s cyber-physical systems (CPSs) are fitted with multiple on-board sensors and computers that make them capable of many civilian and military applications with minimal/no human supervision. Autonomous navigation, transportation, surveillance, and task oriented jobs are becoming more common and ready for deployment in real world applications especially in the automotive, industrial, and military domains. These various enhancements in autonomy are possible thanks to the tight interaction between computation, sensing, communications, and actuation that characterize CPSs. With these increasing capabilities, comes the risk of more security vulnerabilities to cyber-attacks like sensor spoofing with the intent to induce undesired system behavior. An example of this problem was demonstrated by authors in in which GPS data were spoofed to slowly drive a yacht off the intended route.
Many systems, including vehicle technologies, typically have well studied dynamical models and their sensors have specific expected behaviors according to their characterized noise profiles. Malicious attackers aim to compromise a system by diverting system states to unsafe regions, while remaining hidden within system detection boundaries. Despite lying within magnitude boundaries to remain undetected, non-random patterns arise that violate the expected behavior from normal system behavior. For example an attacker with the intention of hijacking an autonomous system while remaining stealthy will manipulate sensor measurements pushing them toward one direction.
In this work, we leverage the known characteristics of the residual – defined as the difference between sensor measurement and state prediction – to build a memoryless runtime monitor to detect non-random behaviors in sensing. To this end, we consider the chi-square detection scheme which creates a test measure to monitor a vector of Normally distributed residuals. To monitor for randomness, we leverage the signed value of the difference between the chi-square distributed test measure and an arbitrary reference point within its known distribution. Systems operating under normal conditions have expected probabilities of whether the test measure should be greater or less than the chosen reference point. Our Cumulative Sign (CUSIGN) dynamic detector, inspired by Cumulative Sum (CUSUM) theory, leverages the history of sign valued differences between the test measure and the reference point, resulting in an alarm rate which is monitored at runtime for attack detection purposes. Thus, as a sensor is compromised, its corresponding residual will leave a trail of non-random behavior and will not follow an expectation.
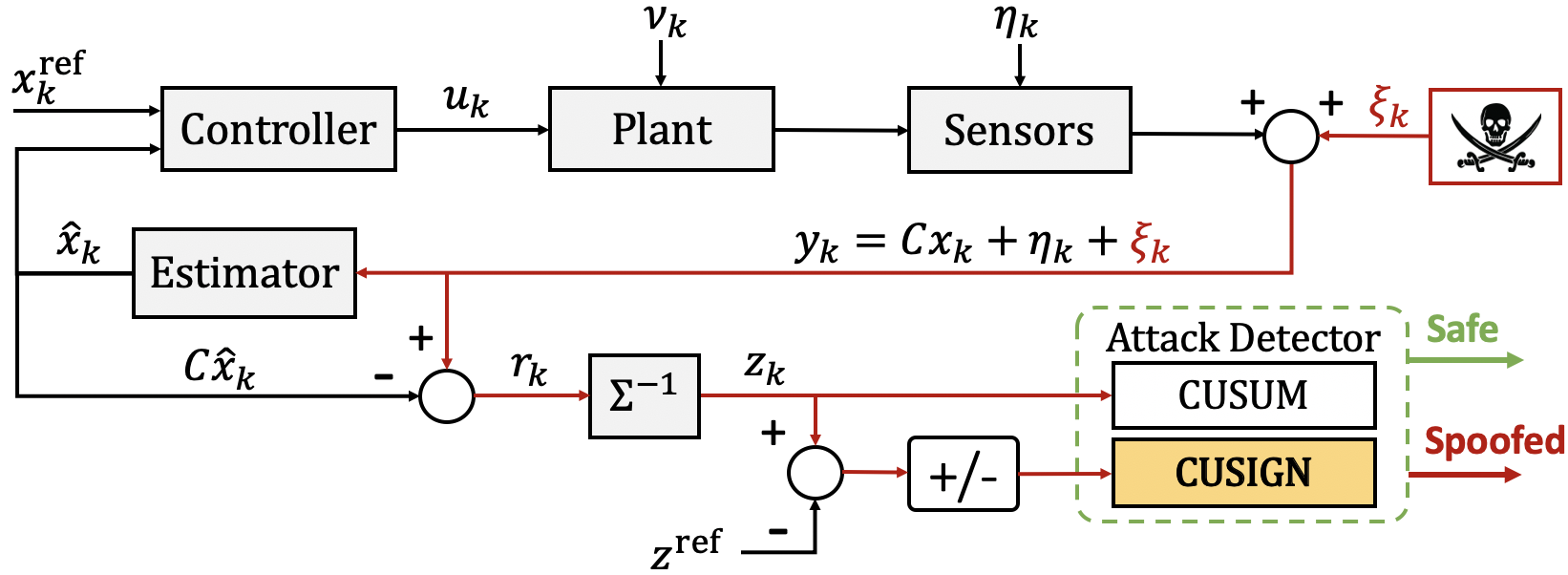
In summary, the main objective of this work is to find stealthy sensor attacks exhibiting non-random behavior within the noise profile of a system in the presence of sensor and process noise. The contribution of this paper is twofold: 1) we propose the CUSIGN detection framework to deal with hidden non-random sensor attacks, typically undetectable by conventional detectors, by monitoring the expected alarm rate associated with consecutive changes of signs in the \textit{test measure}; 2) we introduce a memoryless feature to the CUSIGN detection procedure by leveraging a modified version of Welford’s online algorithm, which we call a Memoryless Run-time Estimator (MRE), that uses a pseudo-window to monitor the alarm rate at run-time, removing the need of storing the entire sequence of data over the duration of the operation. We show empirical results about the MRE with a chosen pseudo-window length to find bounds for detection. Our framework is also combined with the CUSUM technique to create a complete detector framework. Furthermore, we include simulations on a UGV model to validate the proposed detection scheme. For more details, you can find our paper at [IFAC ‘20].