ACC 2021
Serial Randomness Monitoring for Sensor Attack Detection
Abstract: Stealthy false data injection attacks on cyber-physical systems (CPSs) introduce erroneous measurement information to on-board sensors with the purpose to degrade system performance. An intelligent attacker is able to leverage knowledge of the system model and noise characteristics to alter sensor measurements while remaining undetected. To achieve this objective, the stealthy attack sequence is designed such that the detector performs similarly in the attacked and attack-free cases. Consequently, an attacker that wants to remain hidden will leave behind traces of inconsistent behavior, contradicting the system model. To deal with this problem, we propose a runtime monitor to find these inconsistencies in sensor measurements by monitoring for serial inconsistencies of the detection test measure. Specifically, we employ the chi-square fault detection procedure to monitor the magnitude and signed sequence of its chi-square test measure.
Modern cyber-physical systems (CPSs) have been the targets of malicious cyber-attacks due to their growing unsupervised, autonomous capabilities and many entry points to implement an attack. Their expanded complexities supported by an increased number of sensors and computers allow for autonomous capabilities in navigation, warehouse logistics, surveillance, warfare, and industrial operations. With a growing number of vulnerable access points for attackers on increasingly impactful systems in our society, it is crucial to provide tighter security measures to ensure proper performance and safety.
An intelligent attacker is able to implement a malicious attack sequence to manipulate the system of interest, all while remaining undetected. The execution of such a stealthy attack allows the intelligent attacker to degrade system performance and potentially cause damage to the unknowingly compromised system. Previously demonstrated attacks of this nature include cases like: the GPS spoofing of a vessel, different sensor and communication attacks on vehicle technologies, and the infamous Stuxnet attack.
In general, an attacker needs to create inconsistent behavior with respect to the known model in order to hijack a system. In this work, we consider the chi-square detection scheme that generates a scalar quadratic test measure for attack detection. This test measure is extracted from the sum of squares of the residual vector — defined as the vector of differences between sensor measurements and the state prediction. To detect inconsistencies, we monitor the serial behavior of the test measure difference; specifically, we observe the characteristics of consecutive test measures throughout a sequence of measurement data and compare them to an expectation extracted from prior knowledge about the system model. Our proposed Serial Detector is then designed to generate an alarm rate at runtime for detection purposes to discover inconsistent magnitude and sign behavior due to deceptive sensor attacks. For more details, you can find our paper at [IFAC ‘20].
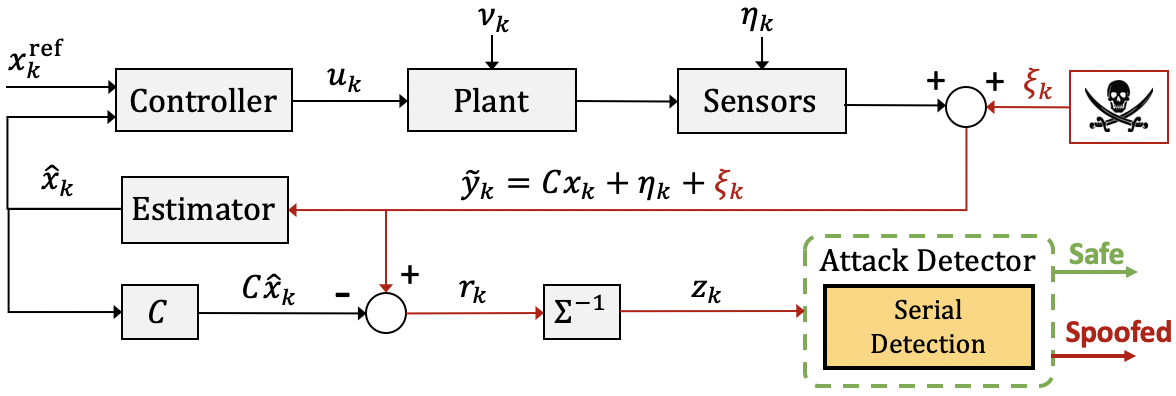
Typical on-board fault detection mechanisms leverage an alarm-based system, such that during nominal conditions the rate of alarm triggers follows a desired alarm rate. Hidden attacks can be defined as designed attack sequences where the attack detector’s alarm rate behaves in the same manner as during nominal, attack-free conditions. If left undetected, an malicious attacker can hijack a system to an undesired state without the system realizing that an attack is present, thus it is imperative to provide tighter security measures for autonomous systems.
