ACC 2020
Windowed Randomness Monitor
Abstract: Malicious attacks on modern autonomous cyber-physical systems (CPSs) can leverage information about the system dynamics and noise characteristics to hide while hijacking the system toward undesired states. Given attacks attempting to hide within the system noise profile to remain undetected, an attacker with the intent to hijack a system will alter sensor measurements, contradicting with what is expected by the system's model. To deal with this problem, in this paper we present a framework to detect non-randomness in sensor measurements on CPSs under the effect of sensor attacks. Specifically, we propose a run-time monitor that leverages two statistical tests, the Wilcoxon Signed-Rank test and Serial Independence Runs test to detect inconsistent patterns in the measurement data. For the proposed statistical tests we provide formal guarantees and bounds for attack detection. We validate our approach through simulations and experiments on an unmanned ground vehicle (UGV) under stealthy attacks and compare our framework with other anomaly detectors.
Today’s autonomous cyber-physical systems are fitted with multiple on-board sensors and computers, allowing for increased capabilities in various applications to perform complex tasks. Consequently, these enhancements increase the risk of cyber attackers to spoofing attacks that can compromise system integrity and safety. With a growing number of vulnerable entry points for attackers on progressively impactful systems within our society, it is imperative to develop more strict security measures to ensure proper performance.
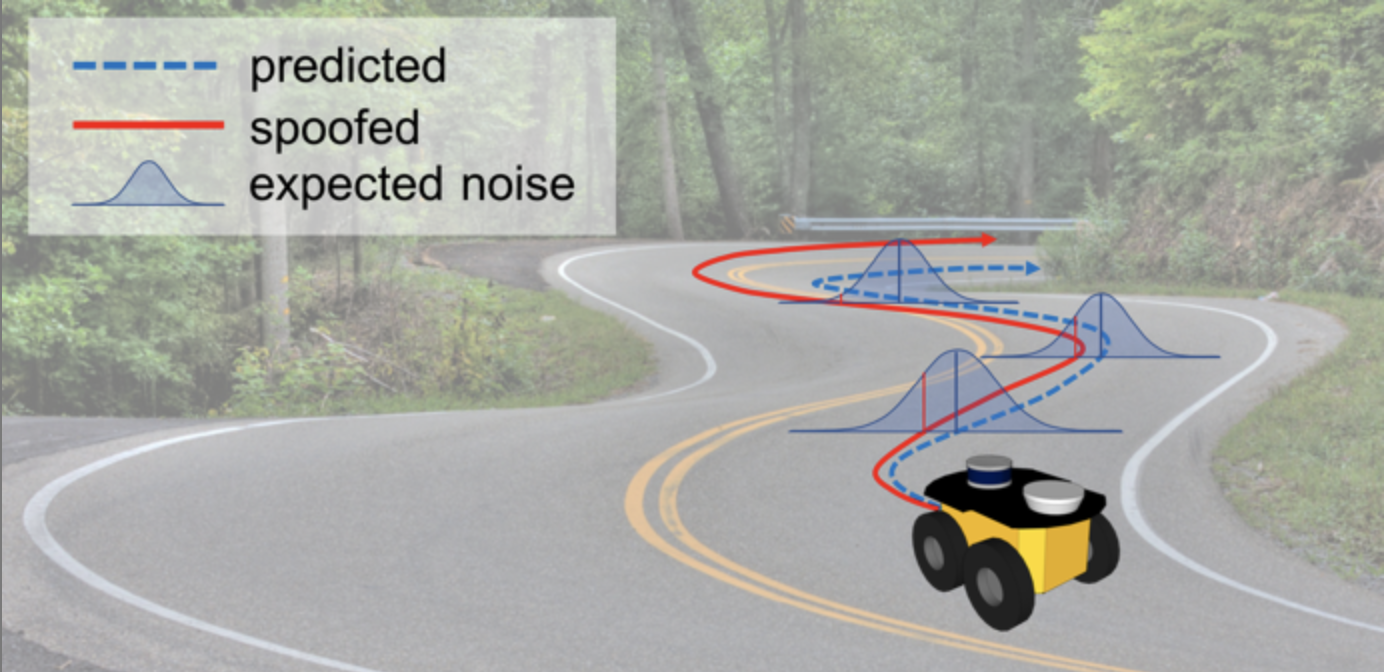
Intelligent attackers are able to implement stealthy attack sequences that hide within system uncertainties in order to remain hidden from typical state-of-the-art detection techniques. However, to effectively hijack a system, an attack must create behavior anomalies (i.e., non-randomness) that contradict the known system model(s). We develop attack detectors that are able to discover non-random events due to sensor cyber-attacks in residual-based detection schemes. With these considerations and problem in mind, in this work, we leverage the known characteristics of the residual -- the difference between sensor measurements and state prediction -- to build a runtime monitor to detect non-random behaviors. To monitor randomness, the non-parametric statistical Wilcoxon Signed-Rank and Serial Independence Runs tests are applied to individual sensors to determine if their measurements are being received randomly. The Wilcoxon test is an indicator of whether the residual is symmetric over its expected value, whereas the Serial Independence runs test indicates whether the sequences of residuals are arriving in a random manner. Thus, the main objective of this work is to find hidden attacks exhibiting non-random behavior within the noise.
Given the nature of the non-parametric statistical tests that we propose, only random behavior of the residual is considered here, leaving the magnitude bounds of the residual un-monitored. Several detectors providing magnitude bounds on attacks have been already researched in the literature, thus in this work we also present a framework to combine existing approaches for magnitude bound detection with the proposed randomness monitor. In doing so, our approach improves the state-of-the-art attack detection by adding an extra layer of checks. With our proposed attack detector implemented on-board a system, we show that previously undetectable attacks can now be found. More details about our approaches with simulation and experiment results can be found in our paper [ACC '20].